As businesses embrace digital transformation, safeguarding sensitive information is critical. Striim 5.0 brings a powerful new feature: Striim Shield, that enables customers to take control of their data encryption through Customer Managed Keys. This innovative feature empowers organizations to securely manage their data before it flows further downstream while ensuring compliance with business policies and industry regulations. Let’s explore what Striim Shield can do for you and how it adds value to your business.
What Does Striim Shield Do?
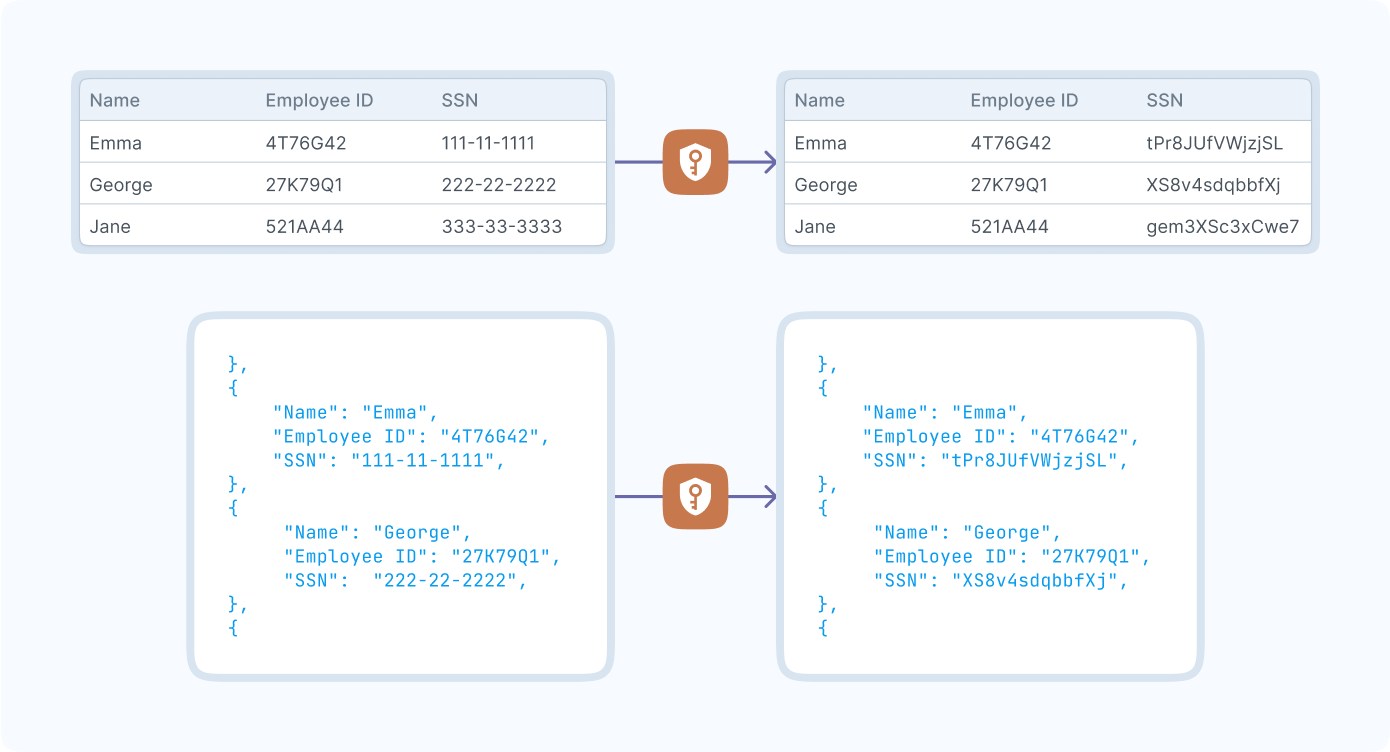
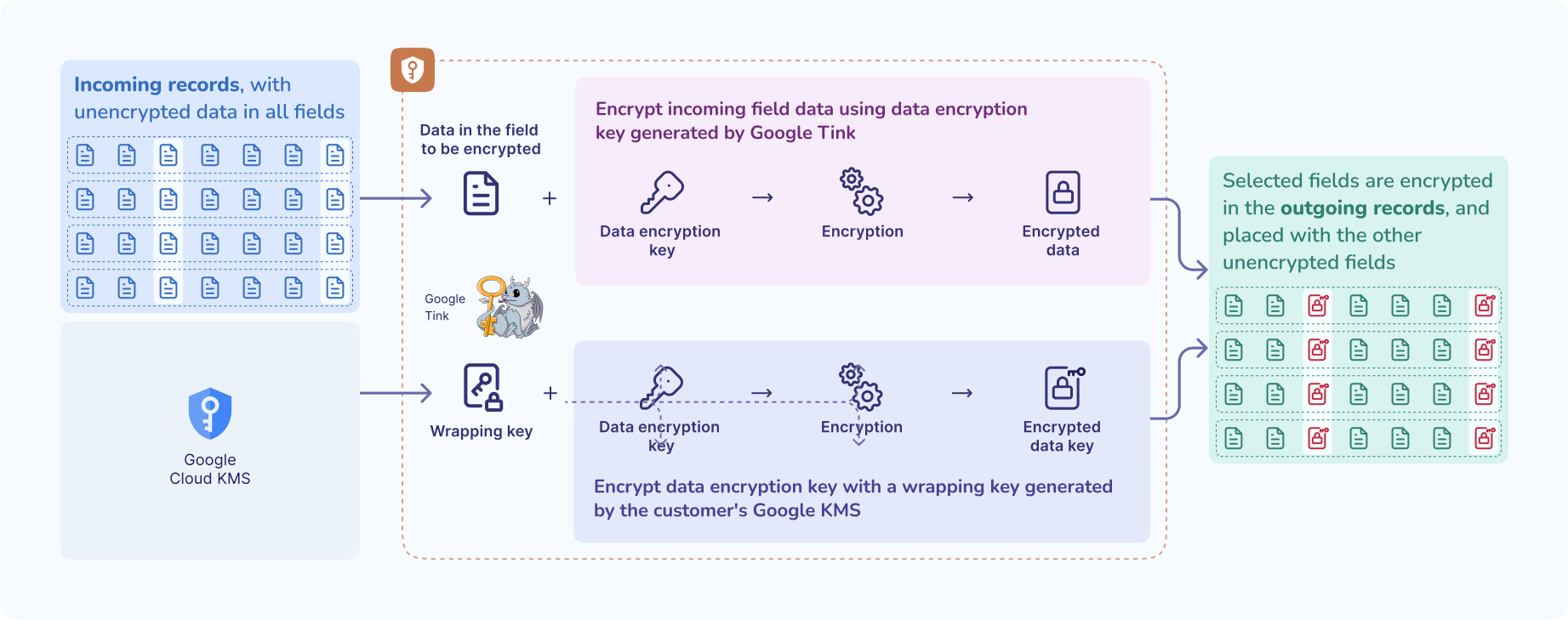
Striim Shield allows users to encrypt specific data fields using keys provided by the customer through Google KMS (Key Management Service). This encryption ensures that sensitive data is securely stored in external targets, while customers maintain control over the encryption keys used. The keys are refreshed regularly (every few days), ensuring that your data stays secure over time. Striim does not manage these keys, giving customers the autonomy to handle their encryption requirements.
How Do You Use Striim Shield?
Users only have to specify the field to be encrypted and link Shield with their Google KMS. Shield uses Google Tink, an open-source encryption library developed by Google Cloud, for envelope encryption operations. The data encryption key is encrypted in-memory with the customer’s Google KMS key and published along with the encrypted data.
Google KMS manages the key operations to ensure that different keys are used during the encryption. There are two modes for key refresh:
- Time-based refresh (set to refresh every 1 day by default)
- Event-based refresh (refreshes after a set number of events)
To decrypt the data, customers must use their Google KMS keys that they provided during the encryption by Shield. Customers can encrypt the encrypted message using Striim Shield, or they can do it outside of Striim using Google Tink.
Want to dive deeper? Check out the doc and explore more.
How Does Striim Add Value?
- Striim Shield delivers several key advantages for businesses: Data Control: Customers retain full control of their data encryption and encrypted data, ensuring sensitive information is protected according to their business needs or regulatory requirements.
- Built for Longevity: Google Tink, maintained by Google Cloud, ensures that Striim Shield is always up to date, backward-compatible, and built to last.
- Security and Transparency: Striim does not create, store or manage encryption keys, guaranteeing that customers maintain full control over the encryption and their sensitive data.
- Granular Encryption: You can encrypt selected columns or fields, enabling more precise control over which data is encrypted before being written to the target.
- Collaboration with Security: Share datasets with internal or external teams without compromising sensitive data, using encryption to manage access to critical fields.
Transform Your Business with Striim Shield – Try It Today!
Striim 5.0’s Striim Shield gives your organization a robust, secure way to manage data encryption while fostering collaboration and ensuring compliance. Ready to power your business with real-time data? Try Striim today with a free trial or book a demo to see it in action.