 The Internet of Things Means You Now Have Less Time to ID Threats
The Internet of Things Means You Now Have Less Time to ID Threats
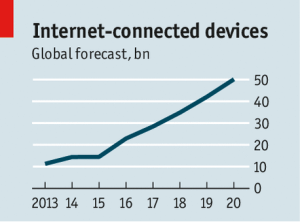
In a July 12 Cyber-security brief “The internet of things (to be hacked)” The Economist discussed the coming explosion of connected devices sharing data in what has commonly become called the Internet of Things (IoT), or as some are now calling the Internet of Everything (IoE). Either term gets you to a place where 18 months from now you have way too much data coming at you to store it all now to process “later”. “Later” will never come and every one of those devices introduces a new potential security threat to your enterprise. The Economist notes:
“There have already been instances of nefarious types taking control of webcams, televisions and even a fridge, which was roped into a network of computers pumping out e-mail spam.”
In this hyper-connected world you need to be continuously monitoring all of devices and traffic on your networks to note interesting correlated events across your infrastructure. WebAction Security Event Processing Data Driven Apps give you a unique insight across your data streams.
Wireless Networks Will Become Saturated
By the nature of IoT devices, wireless is the preferred method of communication. As the number of devices grows, so does the wireless chatter and noise. The chatter is building over all wireless communication channels: WiFi, cellular, Bluetooth, near field communications (NFC), and others. There is no end in sight to the expected growth of wireless connected devices. Networks will need to be fortified and new methods of managing wireless traffic are being considered. Enriching wireless network traffic with rich context and history allows for dynamic network traffic prioritization based on the profiles of your customers. Always make sure that your most important customers always get the best Quality of Service, and know immediately when quality degrades.
Insights Available in Your IoT Streams
The Economist fears that with the loose regulation of connected devices we will see more incidents of hackers working their way into your refrigerator and thermostat. The brief concludes with: “Who needs a smart fridge anyway?” I suppose that is an interesting question, but rather than resisting progress and change (which we know doesn’t work in the long-run), we suggest finding novel ways to immediately identify and neutralize security threats arising from the Internet of Things.
All of those connect devices are reporting their streams back to home base, and home base needs to make some snappy decisions about what to do with the data streams flowing in. At the same time every stream rides on your wireless networks and contains potential threats and useful data signatures. That’s where the WebAction Real-time App Platform shines, monitoring streams to identify patterns in-memory enabling immediate (and informed) action downstream. On the fly your real-time data is correlated across streams, filtered, and enriched with history and context to create highly actionable Big Data Records.
The Internet of Things comes with some very significant blue sky ahead of it and the WebAction Real-time App Platform enables you to take advantage of this new frontier. Request a demo of the WebAction Platform.