Connecting Striim Cloud on Google Cloud Platform to data services behind Striim Forwarding Agent
This topic explains how to use a Striim Forwarding Agent when you prefer to push data to Striim Cloud rather than allowing Striim to initiate direct connections to your sources. It describes how to enable a secure, private connection from a Striim Forwarding Agent (running on-premises or in another cloud) to Striim Cloud (hosted on Google Cloud) by leveraging your GCP VPC and Google Cloud Private Service Connect (PSC).
Overview
The Striim Forwarding Agent reaches Striim Cloud without using the public internet. Traffic stays on private networks: Striim Forwarding Agent → your GCP VPC (via Interconnect/VPN/peering) → PSC endpoint → Striim Cloud.
When the source VM already runs inside GCP, only a PSC connection between your project and Striim is required.
What this topic covers
Using your GCP network as the private transit for Striim Forwarding Agent → Striim Cloud.
Creating a PSC Published Service / Service Attachment (Striim side) and a PSC Endpoint (customer side), or vice-versa per agreed pattern.
Support for Striim Forwarding Agents located:
On-premises (via Cloud Interconnect or VPN into customer GCP VPC)
Cross-cloud (AWS/Azure/Oracle Cloud Infrastructure (OCI)) with private connectivity into customer GCP VPC
GCP (native VMs or Google Kubernetes Engine (GKE) in the customer project)
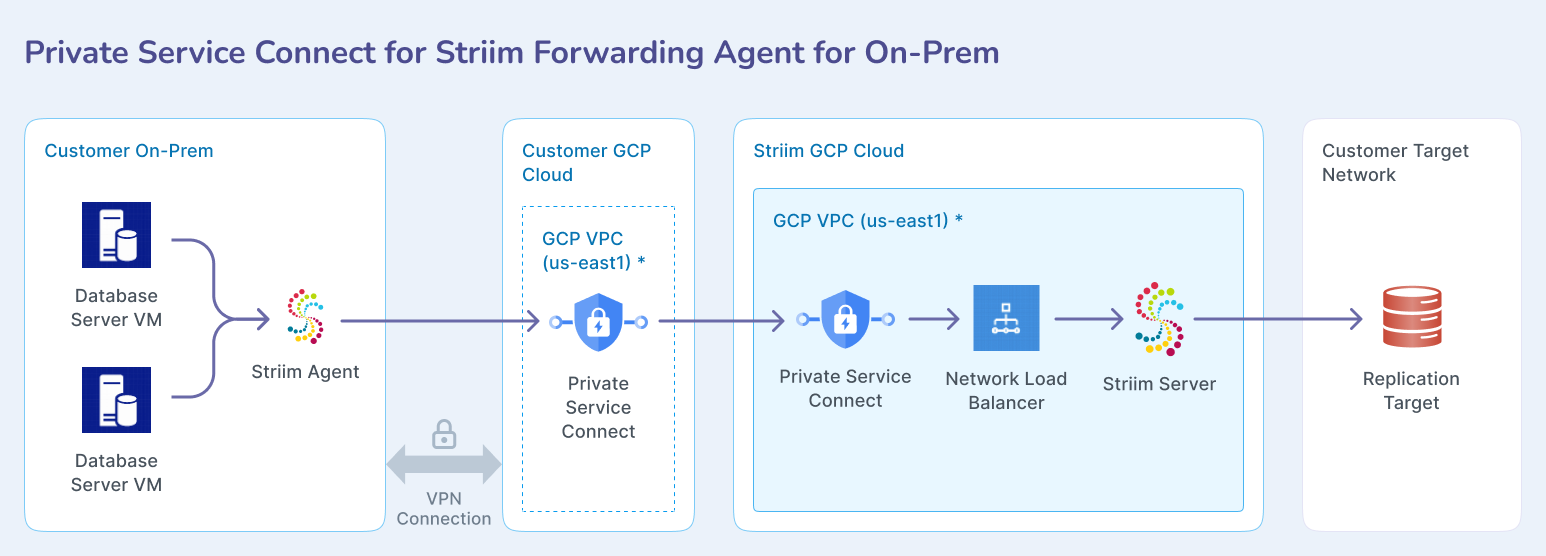
For on-premises Striim Forwarding Agents, the connection routes through your GCP VPC via VPN to reach Striim Cloud privately:
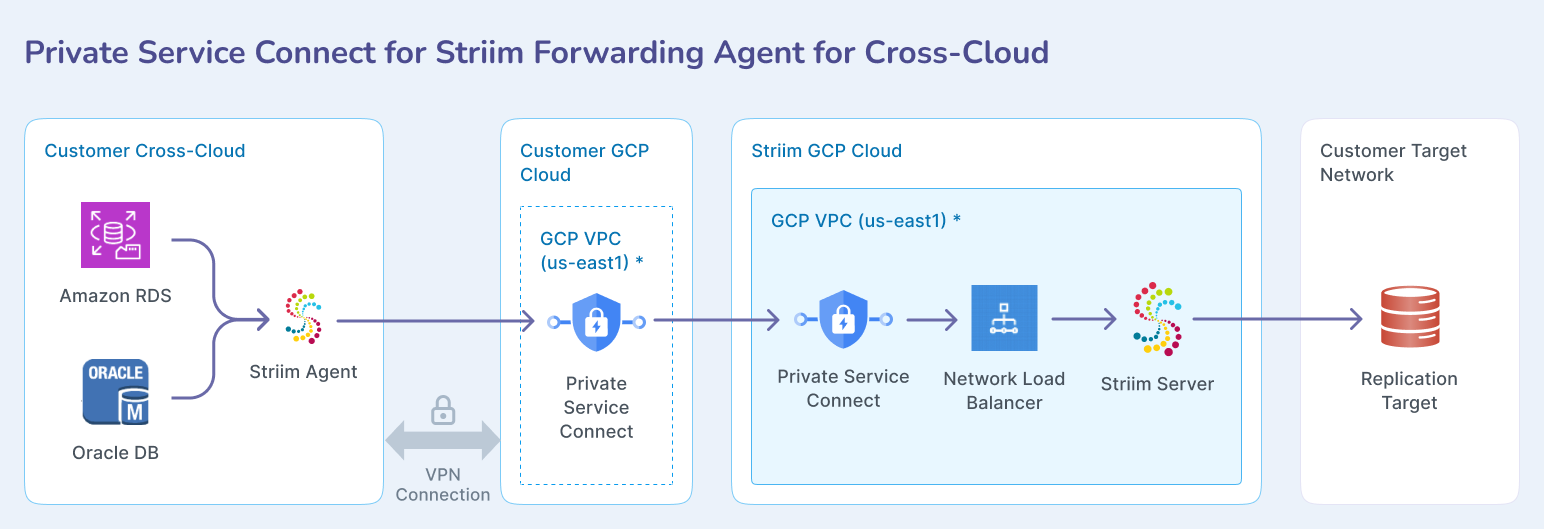
For cross-cloud Striim Forwarding Agents in AWS, Azure, or OCI, the connection routes through your GCP VPC via inter-cloud connectivity to reach Striim Cloud privately:
Prerequisites
A GCP project & VPC capable of hosting a PSC endpoint.
Private connectivity from Striim Forwarding Agent location to the customer GCP VPC (Interconnect, VPN, or peering).
Appropriate IAM to create and approve PSC resources.
VPC firewall rules allowing traffic from the Striim Forwarding Agent to the PSC endpoint and onward to Striim Cloud over ports - 30000, 30002, 30003, 30010-30200.
A Striim service with admin role to the striim cloud account as well as Customer GCP console.
Striim service (sys) password
Prepare customer VPN with on-prem/cross-cloud network
GCP-to-AWS VPN(classic): see Site-to-Site VPN Between GCP and AWS Cloud.
GCP-to-On-prem: see Creating a site-to-site VPN tunnel in Google Cloud (GCP) to set up a Virtual Private Cloud (VPC) network, and configure a Cloud VPN gateway.
Step-by-step process to setup private service connect (PSC)
This process involves coordination between you and the Striim team to establish the PSC connection. The Striim team provides the service attachment, while you create the corresponding PSC endpoint in your GCP project.
Prepare striim network:
The customer submits a request to the prepaid Striim service with Private Service Connect for forwarding agent compatibility
Striim information sharing list for customer:
The Striim team prepares the environment and shares the Private Service Connect attachment with the customer. The PSC attachment looks like:
projects/saas-app1-stg/regions/us-west1/serviceAttachments/k8s1-sa-o2br638g-defau
The Striim team also shares the Striim service sys password to generate the Striim agent key-store password
Create Private service connect connection in customer GCP network:
The customer's GCP VPC network must be in the same region as the Striim service.
Create a subnet to host Private Service Connect.
Create a private static IP address from the psc-subnet IP range.
Create the Private Service Connect connection using the PSC attachment shared by the Striim team.
After successfully creating the PSC, you can check in the GCP console within the private service connect service page, under CONNECTED ENDPOINTS. This PSC will show in Pending state until the request is accepted by the Striim team.
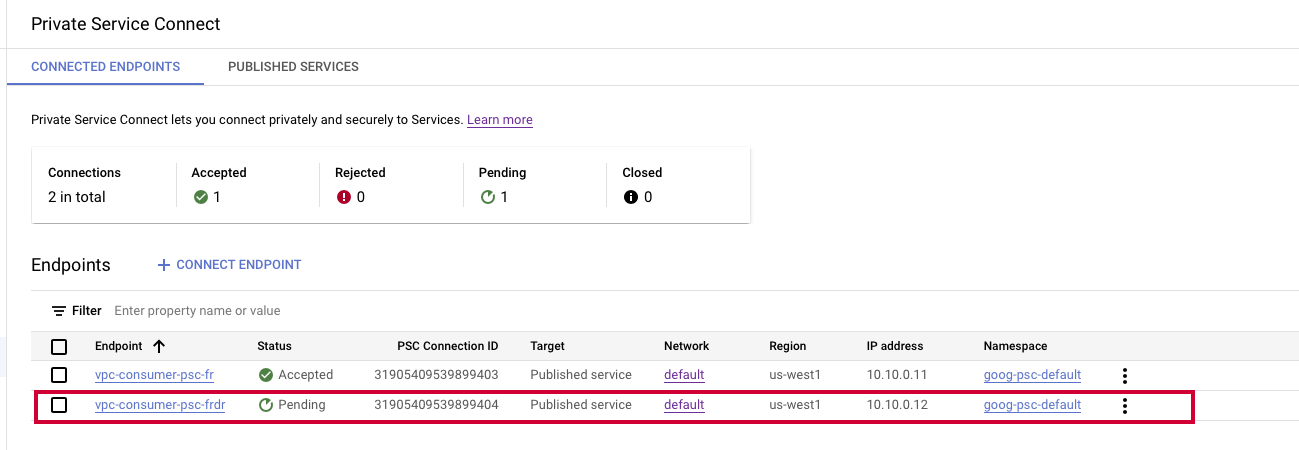
Once the Striim team accepts the connection, the PSC endpoint status will change to Approved.
Test the connection from the customer network:
SSH to the Striim Forwarding Agent VM
Use the telnet command to check connection using PSC endpoint IP e.g. 10.10.0.12
telnet 10.10.0.12 30000
Also try the following ports: 30001, 3003, 30010-30200