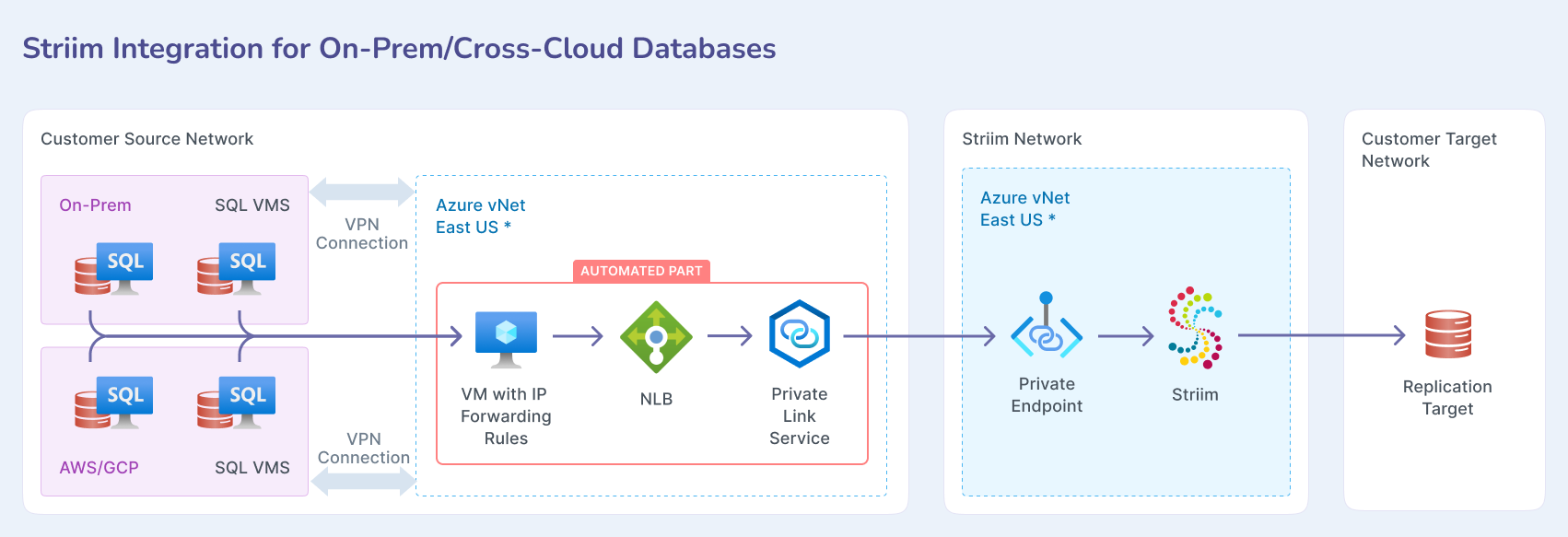
Automating the Azure Private Link integration
Striim provides a Terraform module that automates the above setup for on-premise/cross-cloud sources. The automation is available in the GitHub repository at https://github.com/striim/azure-privatelink-resource-setup-terraform/tree/main. This module provisions a VM (Linux/Windows) with port forwarding, an internal Load Balancer with NAT rules, and an Azure Private Link Service.
Important
This Terraform script creates Azure resources (VMs, Public IPs, LB, Private Link Services, etc.) that may incur charges. Review costs before use.
Prerequisites
Before using this Terraform module, ensure the following:
You must have an existing Azure VNet and subnet for the deployment.
A VPN/ExpressRoute already set up between Azure and your database network.
Your on-premise or cloud databases must be reachable from the Azure vNet.
Permission to create Azure Storage. The Azure storage is used for storing VM scripts temporarily.
Fill out all required fields in the
pass_values.tfvarsfile.
Deploying with Terraform
Deploying the integration requires cloning or downloading the repository, initializing Terraform, planning the deployment, and applying the changes to deploy resources.
To deploy the integration:
Clone or download the repository.
git clone https://github.com/striim/azure-privatelink-resource-setup-terraform.git" cd azure-privatelink-resource-setup-terraform
Initialize Terraform.
terraform init
Plan the deployment by passing the values file.
terraform plan -var-file="pass_values.tfvars"
Apply the changes to deploy the resources.
terraform apply -var-file="pass_values.tfvars"
Verifying the deployment
Once the Terraform apply is completed successfully, you should see the following outputs:
VM information
VM Name: the name of the provisioned VM (
striim-int-vm)VM Public IP: the public IP address assigned to the VM (if applicable)
OS Type Used: Linux or Windows (based on
vm_os_type)
SSH/RDP credentials
For Linux VM: SSH Private Key: a private key will be generated and displayed as a sensitive output.
To connect:
ssh -i ~/.ssh/striim-integration-key azureuser@<vm-ip-address>
For Windows VM: RDP Connection: use the admin username and password for RDP access.
Port forwarding rules (either one, based on OS type)
Linux (iptables) rules applied.
Run the following command inside the VM:
sudo iptables -t nat -nvL
You should see DNAT and SNAT rules applied for the defined
ip_forwarding_targets.Windows (netsh portproxy) rules applied.
Run the following command inside the Windows VM:
netsh interface portproxy show all
Expected output should list port forwarding rules mapping source ports to target database servers.
Internal load balancer
ILB Name:
${base_name}-lbBackend Pool: the VM will be registered as a backend.
Private Link service
Service Alias: the alias for the Private Link Service.
Storage account for scripts (Windows only)
If using Windows, an Azure Storage Account will be created for storing startup scripts.
The VM will download and execute the
config-script.ps1from the storage account.
If everything is working correctly, the VM should successfully forward traffic to the defined database servers.
Configuring and using the deployed resources
This section describes steps to configure and use the deployed resources.
If using a Linux VM, perform these steps to set up SSH:
To export the SSH key:
terraform output -raw ssh_private_key > ~/.ssh/striim-integration-key chmod 600 ~/.ssh/striim-integration-key
To SSH into the VM:
ssh -i ~/.ssh/striim-integration-key azureuser@<vm-ip-address>
To check the port forwarding rules:
For Linux:
sudo iptables -t nat -nvL
To manually create a rule:
iptables -t nat -A PREROUTING -p tcp --dport <source-port> -j DNAT --to-destination <dest-ip>:<dest-port> iptables -t nat -A POSTROUTING -p tcp -d <dest-ip> --dport <dest-port> -j SNAT --to-source $(hostname -i) iptables-save
For Windows:
To check existing rules:
netsh interface portproxy show all
To create a new rule:
netsh interface portproxy add v4tov4 listenport=<port> listenaddress=0.0.0.0 connectport=<port> connectaddress=<dest-ip>
Terraform variables
Populate the following required variables:
Variable name | Description | Example |
|---|---|---|
| Azure subscription ID | "00000000-0000-0000-0000-000000000000" |
| Striim subscription ID | "00000000-0000-0000-0000-000000000000" |
| Public IP to allow access | "45.23.167.23/32" |
| Prefix for resource names | "striim-int" |
| Azure region | "eastus" |
| Azure resource group | "your-azure-rg" |
| Virtual network name | "your-azure-vnet" |
| Subnet name | "your-subnet-name" |
| VM admin username | "azureuser" |
| VM admin password (Windows only) | "your-secure-password" |
| VM SKU type | "Standard_D2s_v3" |
Choose a VM type:
OS type | Terraform configuration |
|---|---|
Linux | Uncomment |
Windows | Uncomment |
Configure port forwarding rules:
Database IP address | Port |
|---|---|
192.168.00.1 | 1433 |
192.168.00.2 | 1435 |
192.168.00.3 | 1438 |
192.168.00.4 | 1440 |
Troubleshooting the integration
The following are common issues:
Error | Solution |
|---|---|
| Ensure the config-script.ps1 file is correctly uploaded to Azure Storage and accessible. |
| Make sure resources with |
| Manually check and apply forwarding rules using iptables (Linux) or netsh (Windows). |
| If deploying a Windows VM, SSH keys are not applicable. |
Security considerations
Observe the following security considerations when using this module:
Do not store passwords in Terraform variables. Use environment variables instead.
Restrict public SSH/RDP access using security groups.
Enable Azure Defender for monitoring security threats.
Use IAM roles to control access to Terraform and Azure resources.
Disclaimers
By using this Terraform module, you agree that:
Striim is not responsible for resource creation, deletion, or costs incurred on your Azure account.
You must review and approve the resources before deploying them.
Ensure your network security policies allow access between Azure and On-Prem environments.
Apply the module in a non-production environment first and verify all resources.
No outbound rules are required from the database network to your Azure vNet.
If necessary, you can clean up the resources as follows:
terraform destroy -var-file="pass_values.tfvars"