Fabric Data Warehouse Writer programmer's reference
Fabric Data Warehouse Writer properties
property | type | default value | notes |
|---|---|---|---|
Azure Account Access Key | encrypted password | the account access key for the storage account you created as described in Initial Fabric Data Warehouse Writer setup, which you can find in Azure at Storage accounts > <account name> > Access keys | |
Azure Account Name | String | the name of the storage account you created as described in Initial Fabric Data Warehouse Writer setup, which you can find in Azure at Storage accounts | |
CDDL Action | String | Process | See Handling schema evolution. If TRUNCATE commands may be entered in the source and you do not want to delete events in the target, precede the writer with a CQ with the select statement Known issue DEV-48379: ALTER TABLE ... ADD PRIMARY KEY is not supported by Fabric, but instead of halting the application will continue as if the command had been successful. |
Client Configuration | String | If using a proxy, specify | |
Column Delimiter | String | If the data to be written may contain the default column delimiter (ASCII / UTF-8 124), specify a different delimiter that will never appear in the data. | |
Connection Profile Name | String | Appears in Flow Designer only when Use Connection Profile is True. See Connection profiles. | |
Connection Retry Policy | String | initialRetryDelay=10s, retryDelayMultiplier=2, maxRetryDelay=1m, maxAttempts=10, totalTimeout=10m | With the default setting, if a connection attempt is unsuccessful, the adapter will try again in 10 seconds ( The adapter will halt when either
If To disable connection retry, set Negative values are not supported. |
Connection URL | String | Provide the full JDBC connection URL with Active Directory password for authentication using the format: jdbc:sqlserver://serverName=<host URL>;encrypt=strict; Authentication=<Active Directory password>; database=<data warehouse name> | |
Excluded Tables | String | If | |
External Stage Connection Profile Name | String | Appears in Flow Designer only when Use Connection Profile is True. See Connection profiles. | |
Ignorable Exception Code | String | Set to TABLE_NOT_FOUND to prevent the application from terminating when Striim tries to write to a table that does not exist in the target. See Handling "table not found" errors for more information. Ignored exceptions will be written to the application's exception store (see CREATE EXCEPTIONSTORE). | |
Mode | String | MERGE | With the default value of MERGE, inserts and deletes in the source are handled as inserts and deletes in the target. With this setting:
For more information about Set to APPENDONLY to handle all operations as inserts. With this setting:
|
Optimized Merge | Boolean | False | Appears in Flow Designer only when Mode is MERGE. Set to True only when Mode is MERGE and the target’s input stream is the output of an HP NonStop reader, MySQL Reader, or Oracle Reader source and the source events will include partial records. For example, with Oracle Reader, when supplemental logging has not been enabled for all columns, partial records are sent for updates. When the source events will always include full records, leave this set to false. Set to True also when the source is Oracle Reader and the source table includes BLOB or CLOB columns When Optimized Merge is True, each primary key update is handled in a separate write operation. If the source has frequent primary key updates, this may lead to a decline in write performance compared with Optimized Merge = False. |
Parallel Threads | String | Creates multiple instances of writer for better performance. See Creating multiple writer instances. Not supported when Mode is MERGE. | |
Password | encrypted password | Microsoft Fabric password. | |
Tables | String | The name(s) of the table(s) to write to, in the format Table names are case-sensitive. You can provide multiple mappings with a semicolon as a separator. For example: You can also provide wildcards to specify table names. For example: Optionally, specify | |
Upload Policy | String | eventcount:10000, interval:5m | The upload policy may include eventcount and/or interval (see Setting output names and rollover / upload policies for syntax). Events are buffered locally on the Striim server and sent as a batch to the target every time either of the specified values is exceeded. |
Trusted Workspace Access | Boolean | False | Set to True to enable trusted workspace access for secure connectivity between Fabric workspaces and private Azure Storage accounts. When enabled, Fabric Data Warehouse Writer uses Fabric workspace identity to access the private storage account through trusted workspace access instead of public network access. Requires prior configuration of workspace identity, storage account role assignments, trusted workspace access, and private endpoints. See Using trusted workspace access with Fabric Data Warehouse Writer for setup instructions. |
Use Connection Profile | Boolean | See Connection profiles. | |
Username | String | Microsoft Fabric username. |
Using manual OAuth with Fabric Data Warehouse
Register and configure an application
Register an application with the Microsoft identity platform as described in Learn / Microsoft Entra / Microsoft identity platform / Quickstart: Register an application with the Microsoft identity platform.
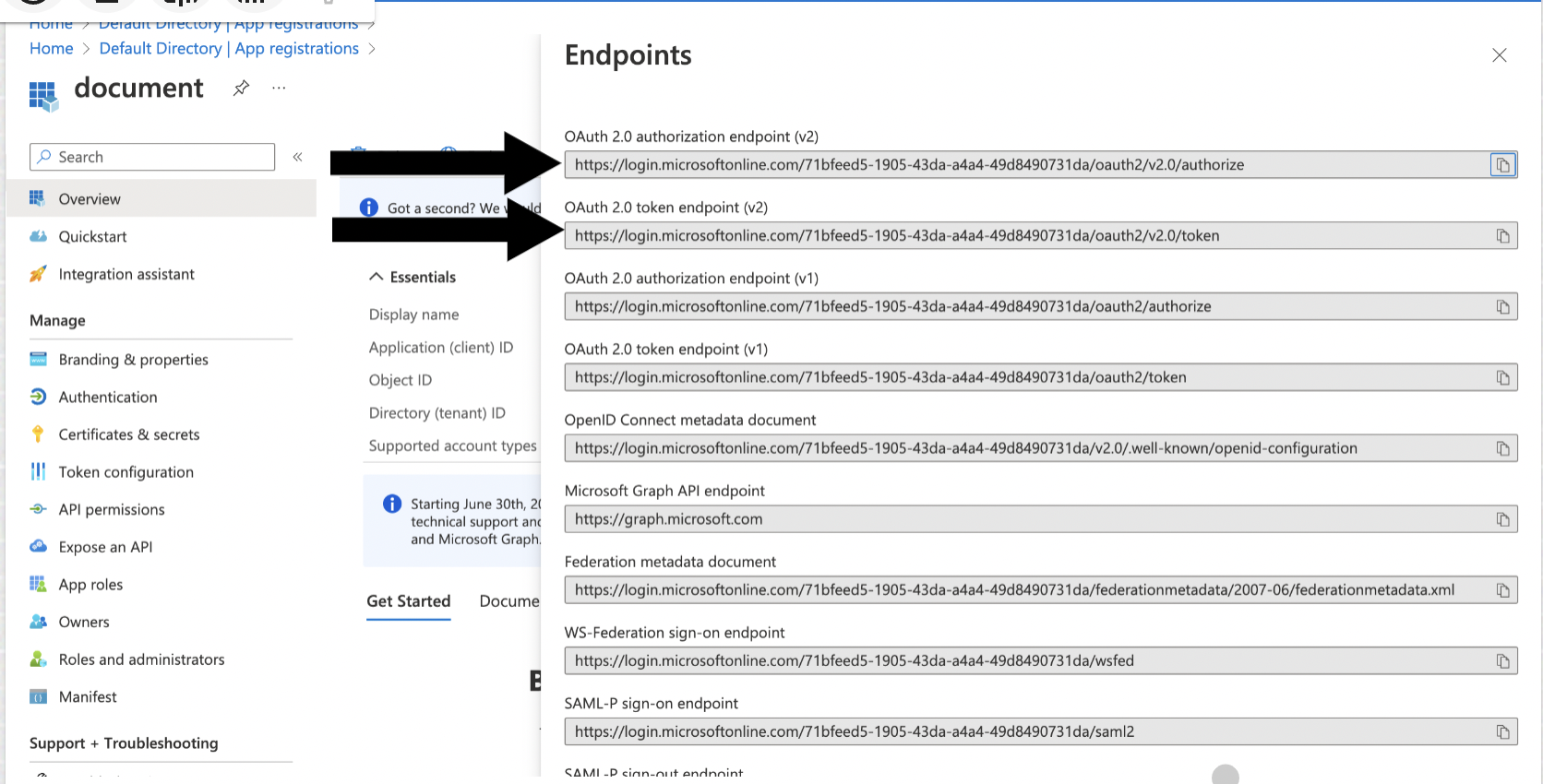
Note the Client (application) ID, Tenant (directory) ID, Client Secret, Authorize Endpoint, and Token Endpoint, you will need them when creating the connection profile.
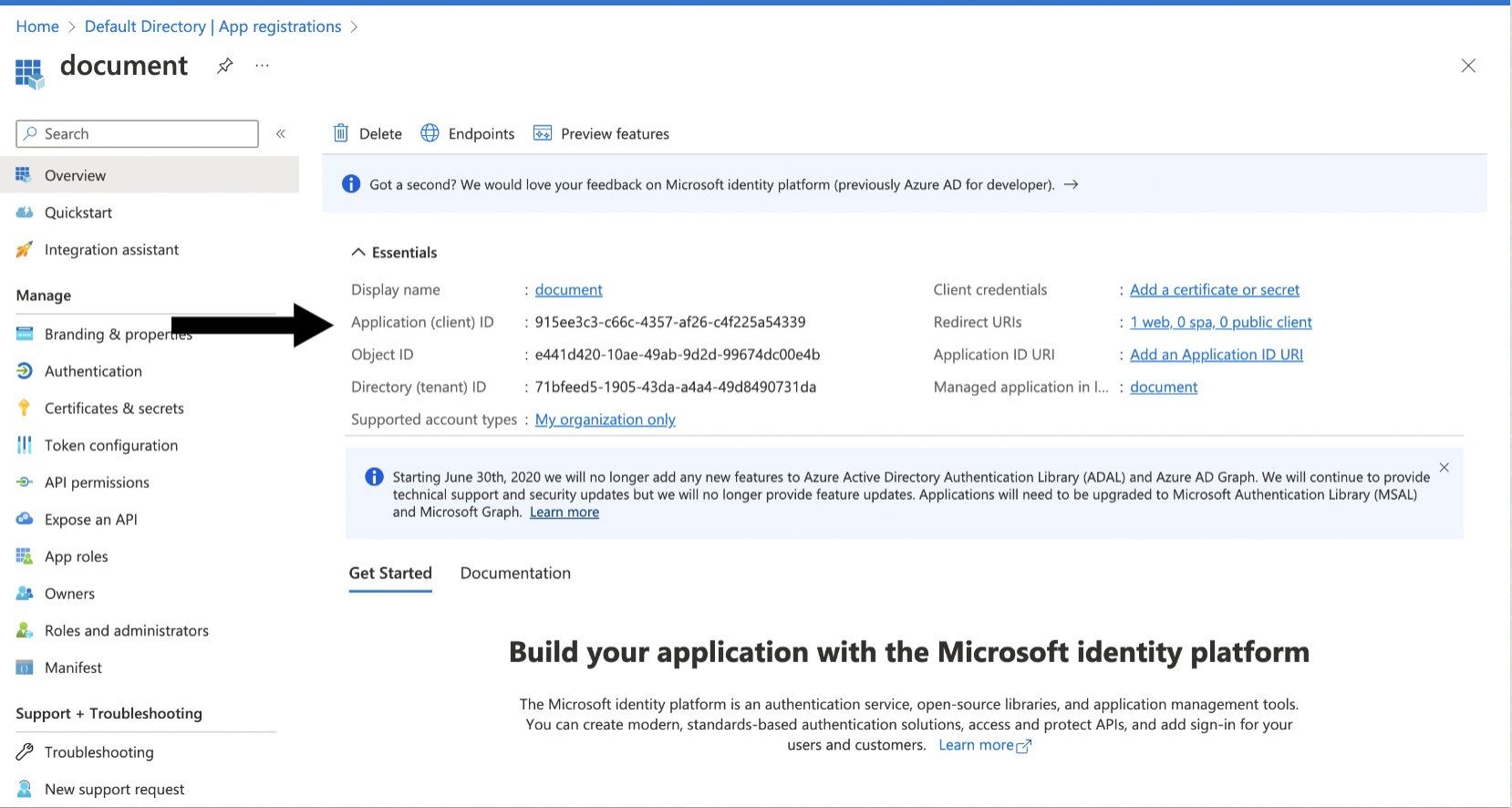
Go to Certificates and Secret and click New Client Secret. Note the value of the secret, you will need it when creating the connection profile.
Go to the registered app, select API permissions, and add the Azure SQL Database (user_impersonation) permission.
Generate the refresh token using a web browser and curl
Call the authorization endpoint by pasting the following into your browser's address bar, replacing
<tenant ID>and<client ID>with the values from "Register and configure an application" and<state>with a random number or some encoded information. To validate the integrity of information exchange, verify that this state value matches the one that in the response payload later in this procedure.https://login.microsoftonline.com/<tenant ID>/oauth2/v2.0/authorize?client_id=<client ID> &response_type=code &redirect_uri=http%3A%2F%2Flocalhost &response_mode=query &scope=https%3A%2F%2Fdatabase.windows.net%2F.default%20offline_access &state=<state>
When prompted, log in as a user with access to the Fabric data warehouse. The browser will return a URL containing an authorization code (the portion between
code=and&state).http://localhost/?code= 0.ARsA1e6_cQUZ2kOkpEnYSQcx2uiQ8dwVo7tCoLGGBj_xw0AbAAA.AgABAAIAAAD--DLA3VO7QrddgJg7WevrAgDs _wUA9P_wji3IyHTg8MQUOqXFtdwUIwVEnR4oCGj0P_l3JfxA3XNfyKczWKpfI87VOu2xrgPodU6y3cs7uyFsy66iia FVMyUd9tIQijRur2mn6lI3OSJHKBHWaVs0Ii8FKQmWJxHRaxUctfJ_Fd9b_ZwmLSSK0pDqTEykK79I_jUXTCsChqq2 R30ztAPHmbwTcu4tTbTLLCuX1O1Kho2wq4KsMl3DQTPciHjXcNJ8Qz0rE909Hn7-wxliNstT3xbYj8V7g1aC3_3N_h jZk7RK6VBmgoStBXcMzckGB0ec34g1p4j7YCh5qAhyNX7lePy1m0IOX88XghY2mFlN_UiotZIwCkA2ZNzTEpxnFhOy L6JilQSGLOoQtP1VGL91ZmB6okhsEZbI8IvJqLvnpwz0N3HMpPJ3jQTQXCVGnla7vQAWyKHBuhRNEA84q8s37E6N-u N3BV16ym_zQWmIAcdgTPMIlbrKbnbpjbv6sbg3uMSs3Chq9mDawxJrh_atw &state=12345&session_state=bf8f7e74-bc50-47a9-a1ee-0db219cb06b0#
Using curl, execute the following command, replacing <client ID> and <client secret> with the values from "Register and configure an application" and
<authorization code>with the string from the previous step. Note the value of the returned refresh token, you will need it when creating the connection profile..curl -X POST -H 'Content-Type: application/x-www-form-urlencoded' \ https://login.microsoftonline.com/<tenant-id>/oauth2/v2.0/token \ -d 'client_id=<client ID>' \ -d 'client_secret=<client secret>' \ -d 'scope=https%3A%2F%2Fdatabase.windows.net%2F.default%20offline_access' \ -d 'code=<authorization code>' \ -d 'redirect_uri=http%3A%2F%2Flocalhost' \ -d 'grant_type=authorization_code' \ -d 'state=12345'
Create a connection profile
Create an Fabric Data Warehouse connection profile (see Connection profiles).
Using trusted workspace access with Fabric Data Warehouse Writer
This topic describes how to configure Fabric Data Warehouse Writer to use trusted workspace access for secure connectivity between Fabric workspaces and private Azure Storage accounts. Trusted workspace access allows Fabric workspaces to securely access private Azure Storage accounts without exposing them to the public internet.
Why use trusted workspace access
Trusted workspace access provides the following benefits:
Enhanced security through private network connectivity.
Compliance with organizational security policies requiring private storage.
Seamless integration between Fabric Data Warehouse and Azure Storage.
Prerequisites
Before configuring Fabric Data Warehouse Writer with trusted workspace access, ensure you meet the following requirements.
Striim Cloud requirements
A running Striim Cloud service (Azure deployment) with sufficient credits.
Access to the Striim Cloud service administration console.
Azure and Fabric requirements
Fabric workspace permissions:
Permission to create a Fabric workspace, or access to an existing Fabric workspace with Admin or Contributor role.
Azure Storage permissions:
Permission to create storage accounts.
Permission to add role assignments to storage accounts.
Azure deployment permissions:
Permission to create custom ARM template deployments in Azure.
Data flow
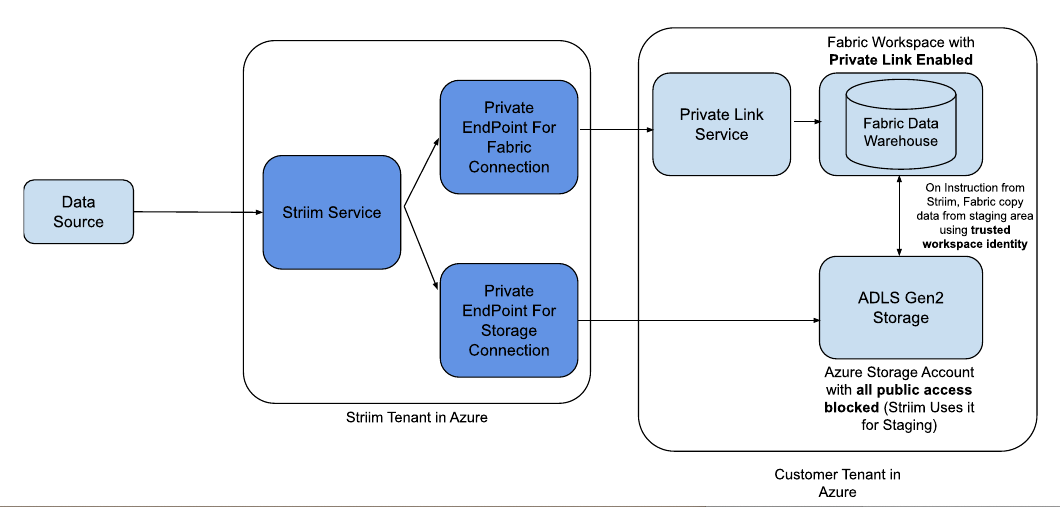
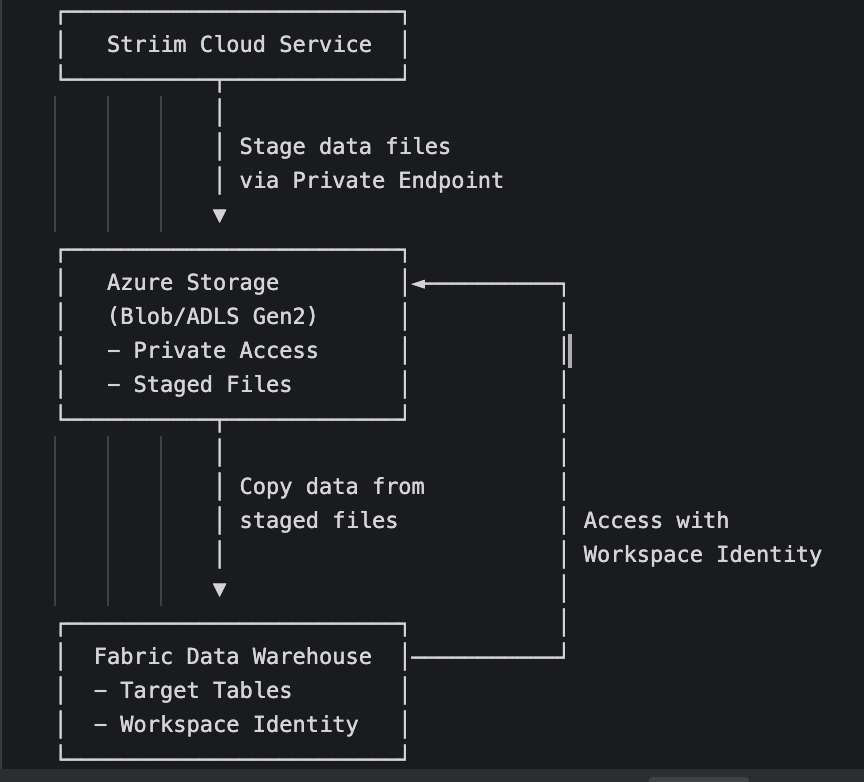
When using trusted workspace access, Fabric Data Warehouse Writer copies data from staged files in Azure Storage to Fabric Data Warehouse tables. The data flow follows these steps:
Striim writes staging files to the private Azure Storage account via a private endpoint.
Fabric Data Warehouse Writer initiates the copy operation.
The Fabric workspace accesses the staging files through trusted workspace access using workspace identity.
Data is loaded into the target Fabric Data Warehouse tables.
Set up workspace and workspace identity in Fabric
Create a Fabric workspace with workspace identity enabled to allow secure access to Azure resources.
Navigate to the Microsoft Fabric portal.
Create a new workspace with a capacity attached.
Enable workspace identity for the newly created workspace by navigating to Workspace settings > Workspace identity and clicking + Workspace identity.
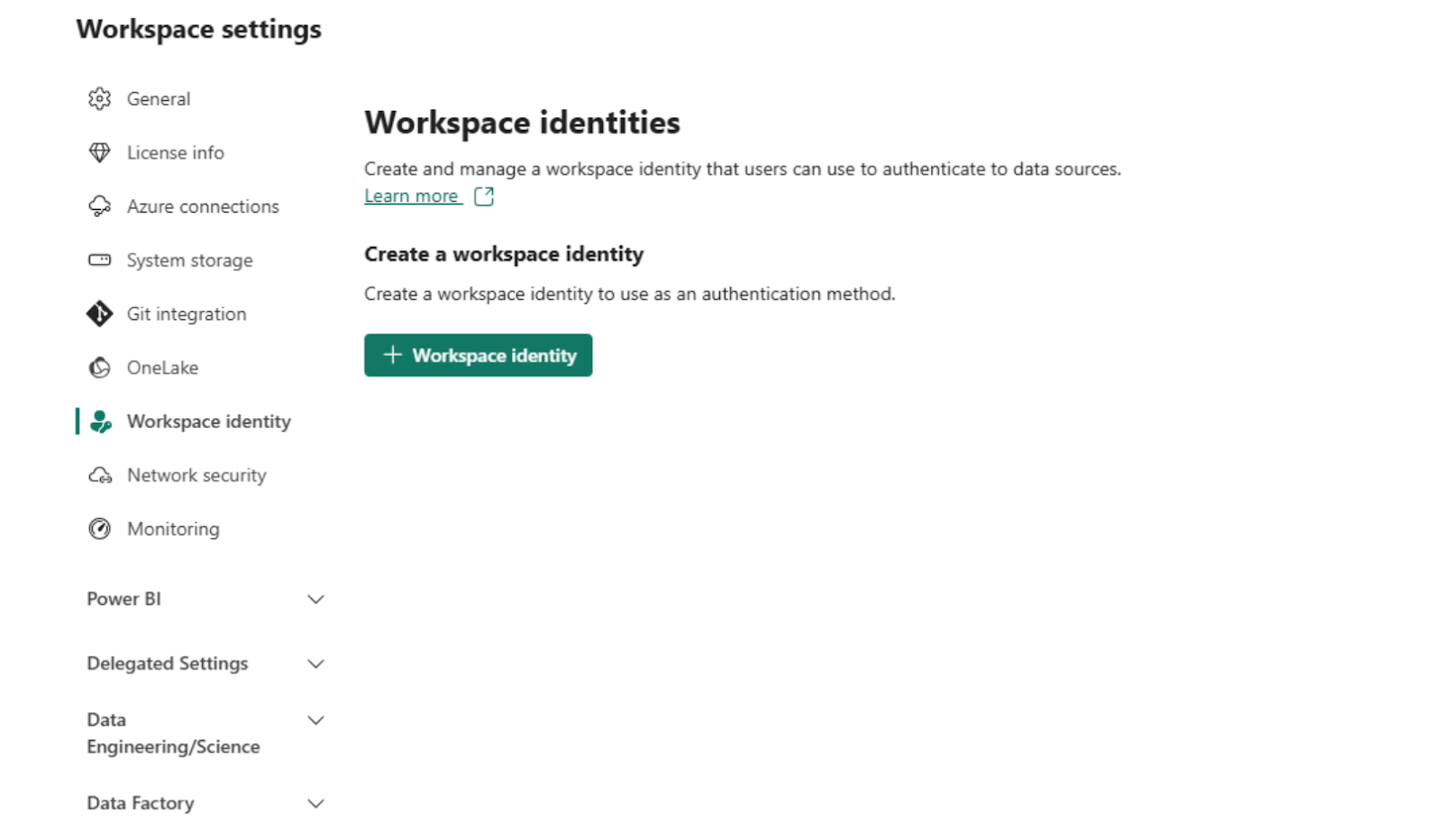
For detailed steps, refer to the Fabric workspace identity section in Microsoft documentation.
Set up storage account in Azure
Create a private Azure Storage account with appropriate role assignments to ensure secure data staging.
Create the storage account
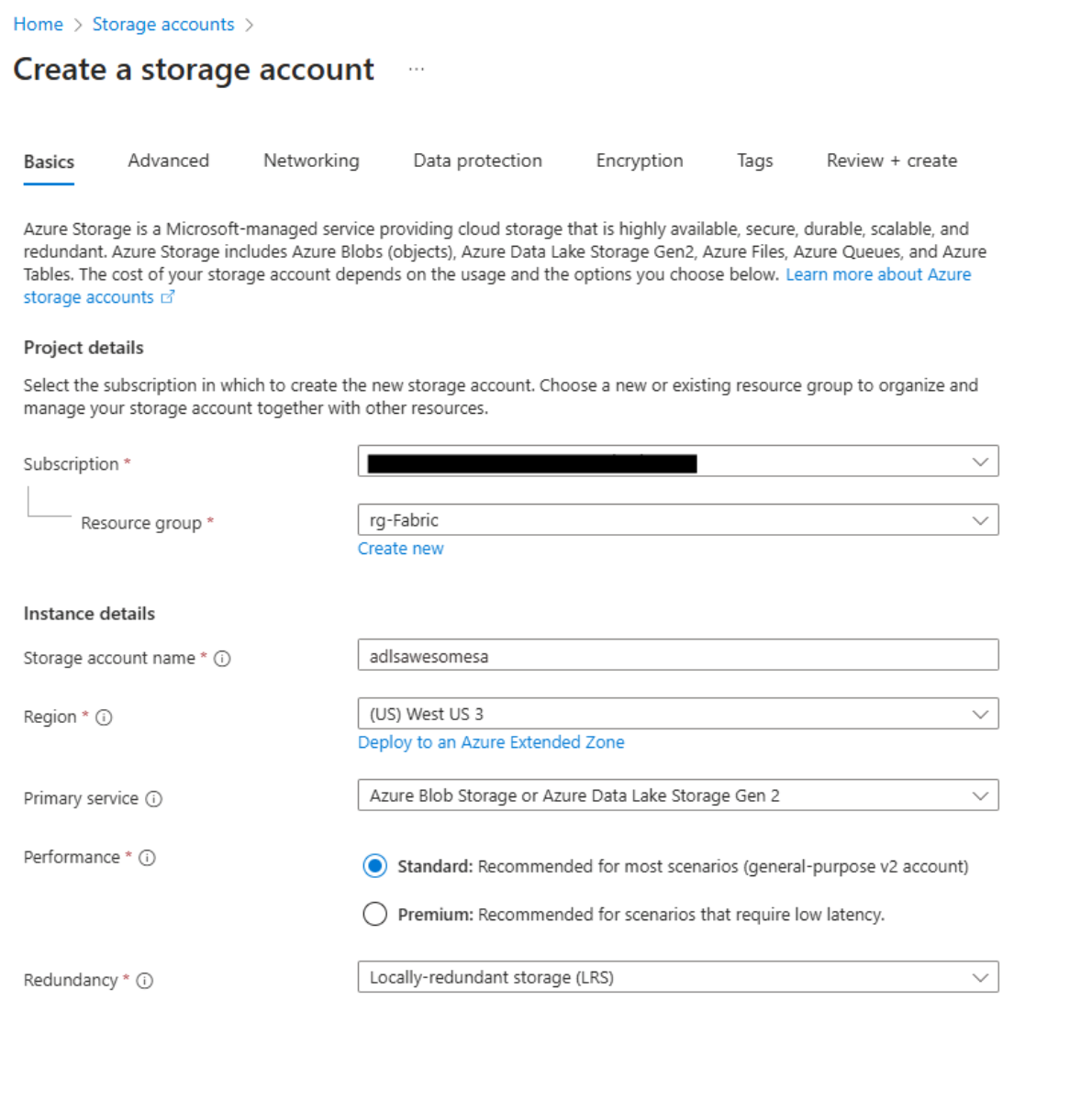
Navigate to Azure Portal.
Create a new storage account with Azure Data Lake Storage Gen2 enabled.
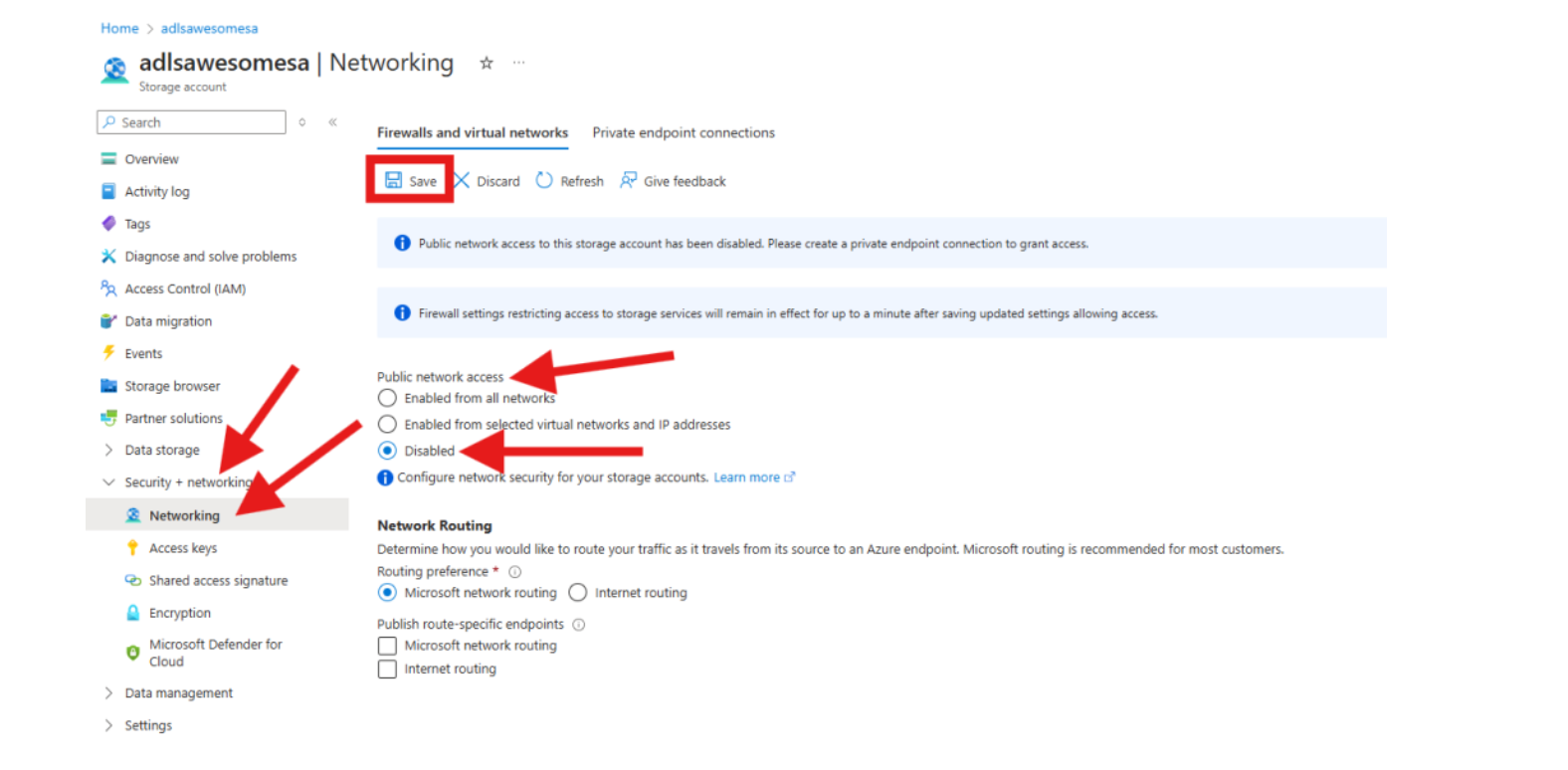
In the storage account networking settings, set Public network access to Disabled to ensure private connectivity.
Assign role permissions
Assign the Storage Blob Data Contributor role to the Fabric workspace identity and authorized user accounts.
Navigate to Access Control (IAM) in the storage account.
Select Add role assignment.
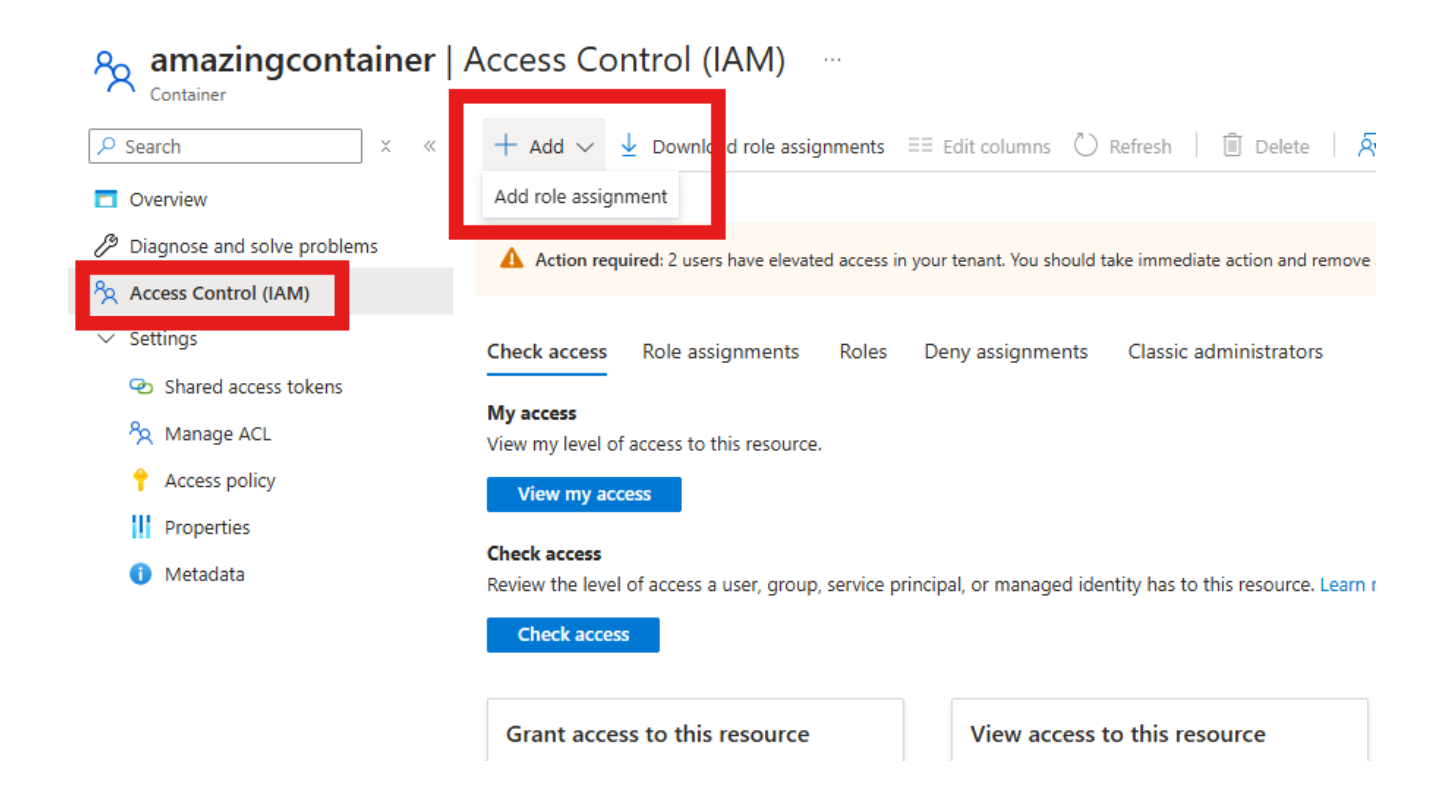
Select Storage Blob Data Contributor as the role.
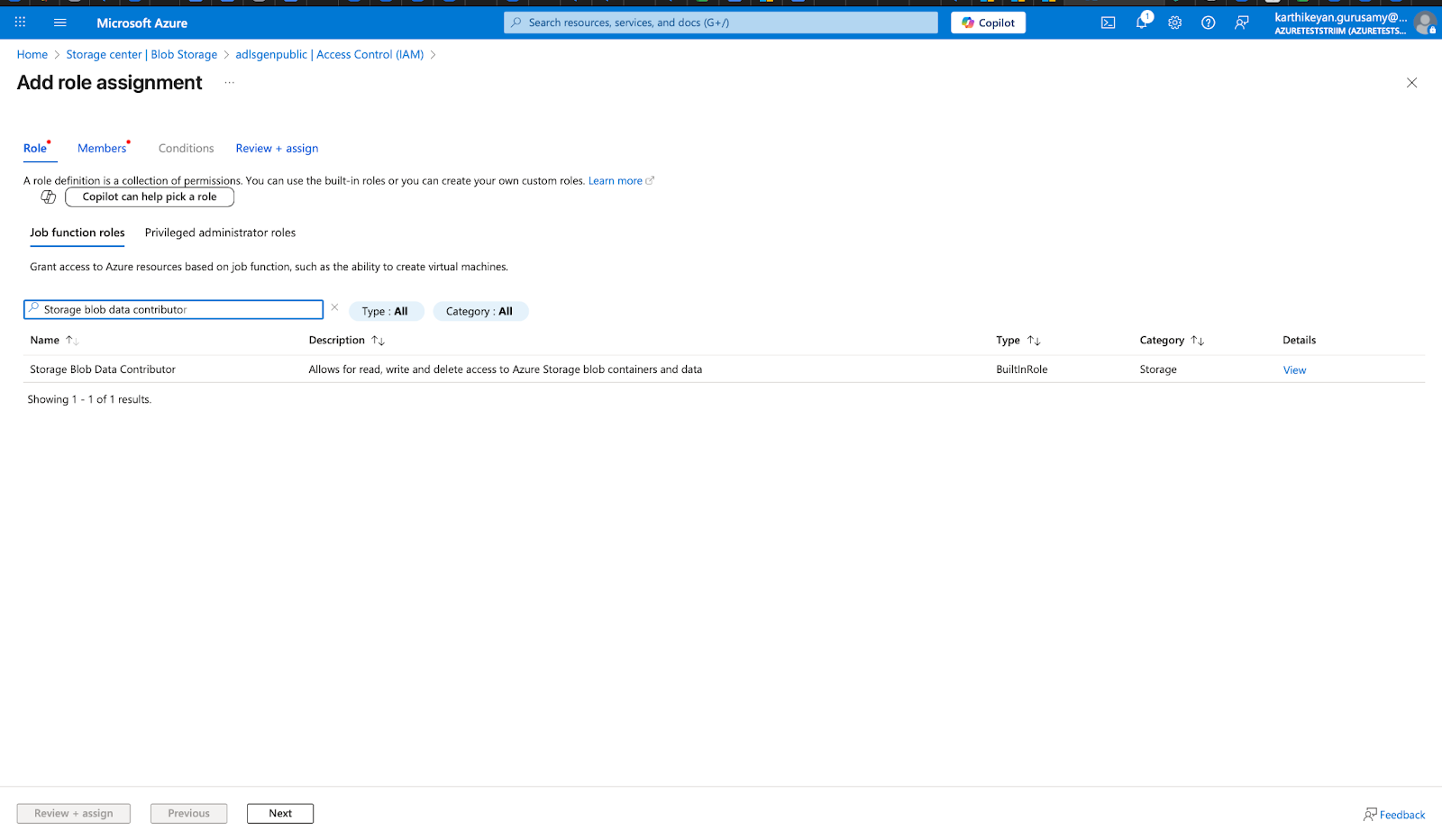
Add the Fabric workspace identity and authorized user accounts as members.
Review and assign the role.
For more details, refer to Grant the Fabric Workspace Identity Access to the Storage Account in Microsoft documentation.
Set up trusted workspace access for storage account
Enable trusted workspace access to allow the Fabric workspace to access the private storage account.
Prepare a custom ARM (Azure Resource Manager) template for trusted workspace access.
In the Azure Portal, search for Deploy a custom template and select it.
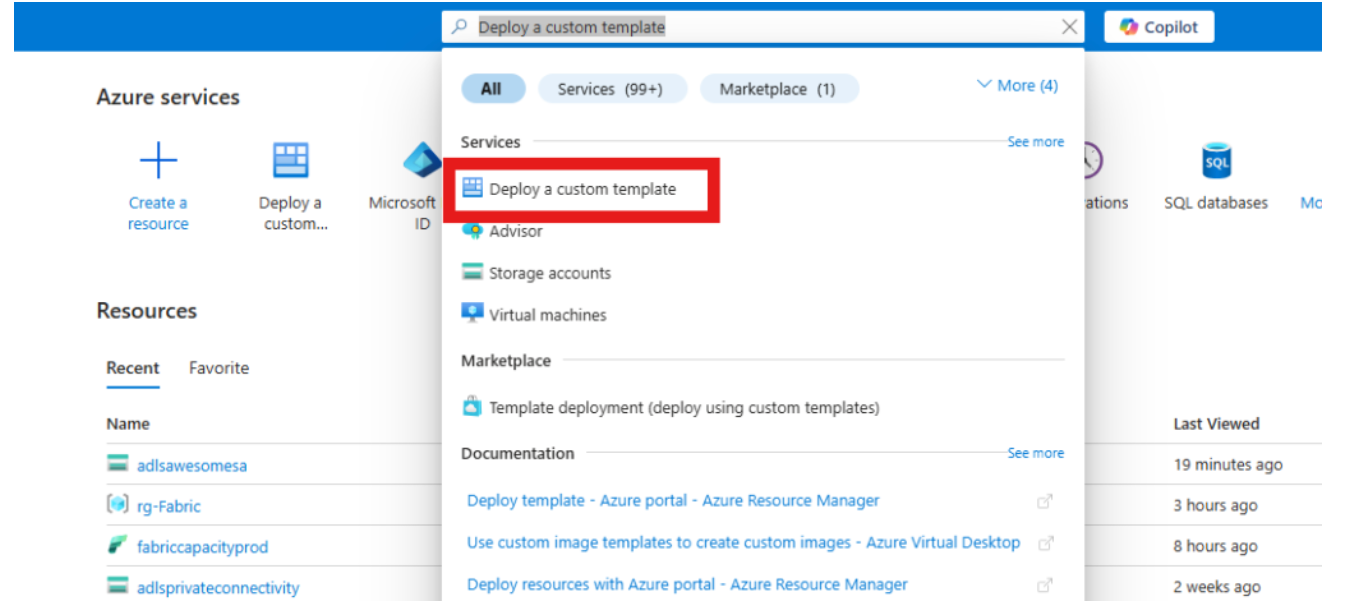
Select Build your own template in the editor.
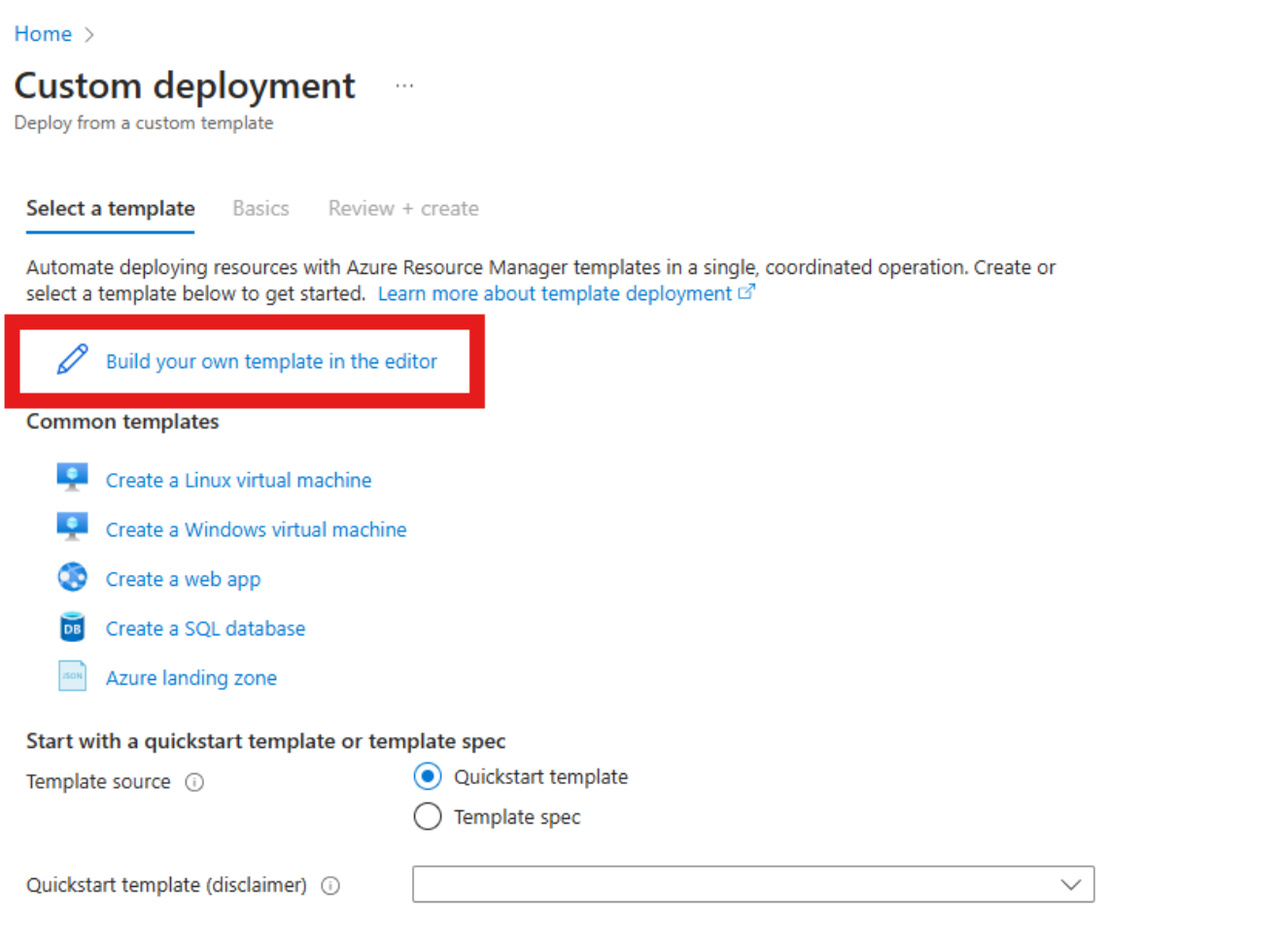
Configure the ARM template deployment parameters, including the storage account name, workspace ID, and resource group settings.
Review and validate the template configuration before initiating the deployment.
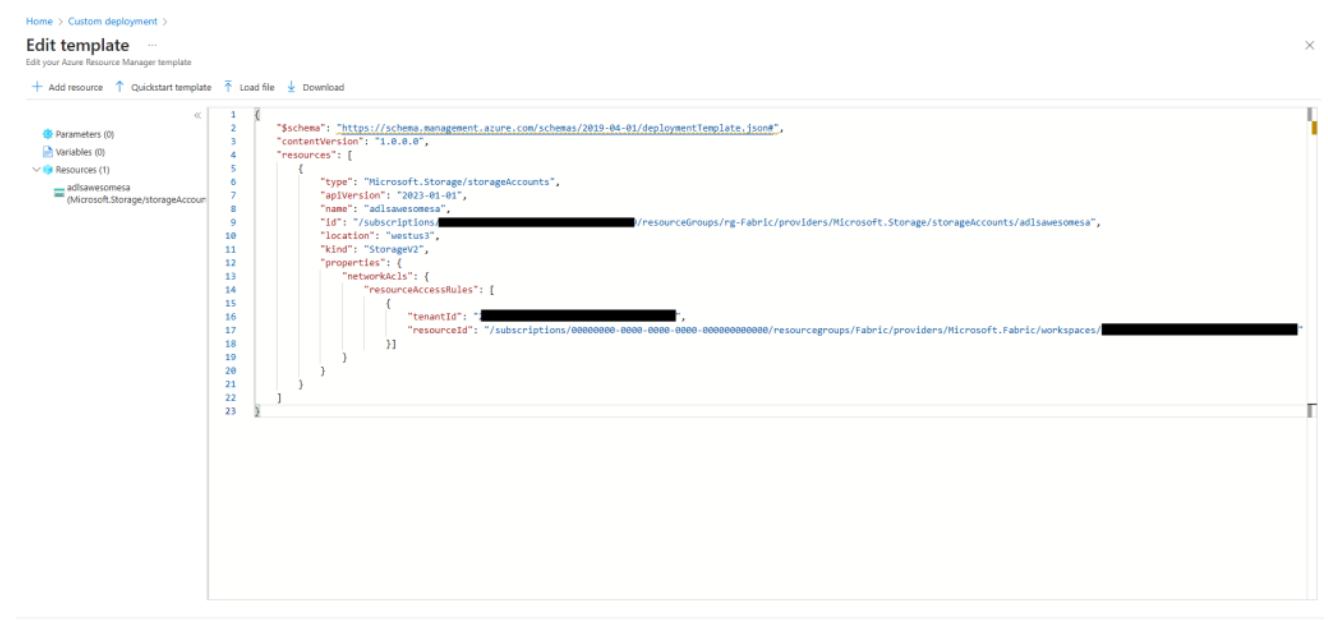
Deploy the custom ARM template to your Azure subscription.
After deployment completes, verify that trusted workspace access is enabled in the storage account's networking settings.
For more details, refer to Enable Trusted Workspace Access in Microsoft documentation.
Set up a private endpoint to the storage account
Create a private endpoint connection from Striim Cloud to Azure Storage to enable secure communication between Striim and the private storage account.
Navigate to the Striim Cloud service where you want to deploy your applications.
Under Secure Connection, click the Private Endpoints tab.
Click Create Private Endpoint.
Fill in the following details:
Name: Enter a descriptive name for your private endpoint connection.
Service Alias: Copy the Resource ID from the Azure Storage Account overview page.
Target Sub-resource: Enter
blob. Fabric Data Warehouse Writer uses the blob endpoint for uploading stage files.
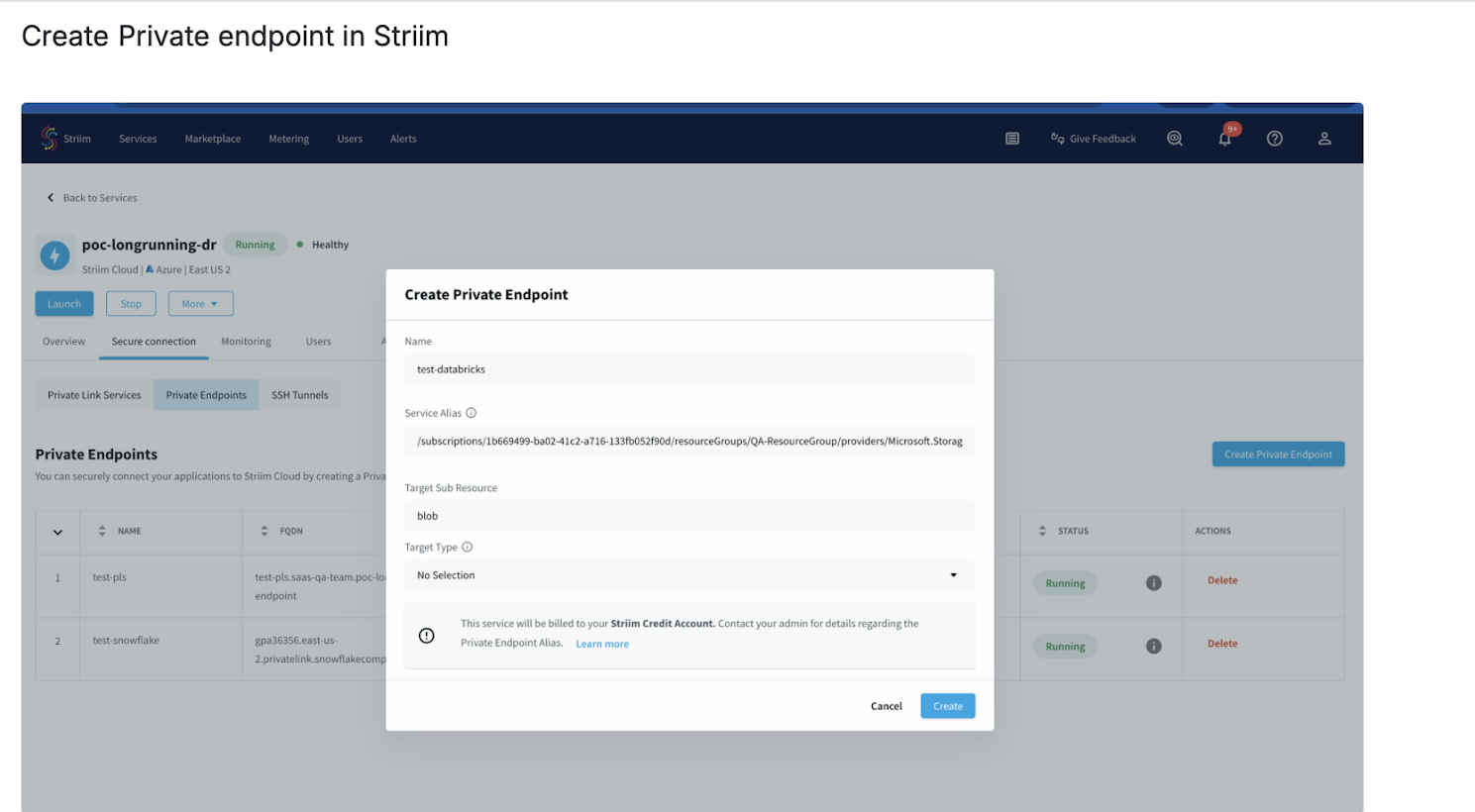
Click Create to initiate the private endpoint approval process.
Approve the private endpoint request
Navigate to your Azure Storage Account.
Go to Networking > Private endpoint connections.
Review the pending approval request.
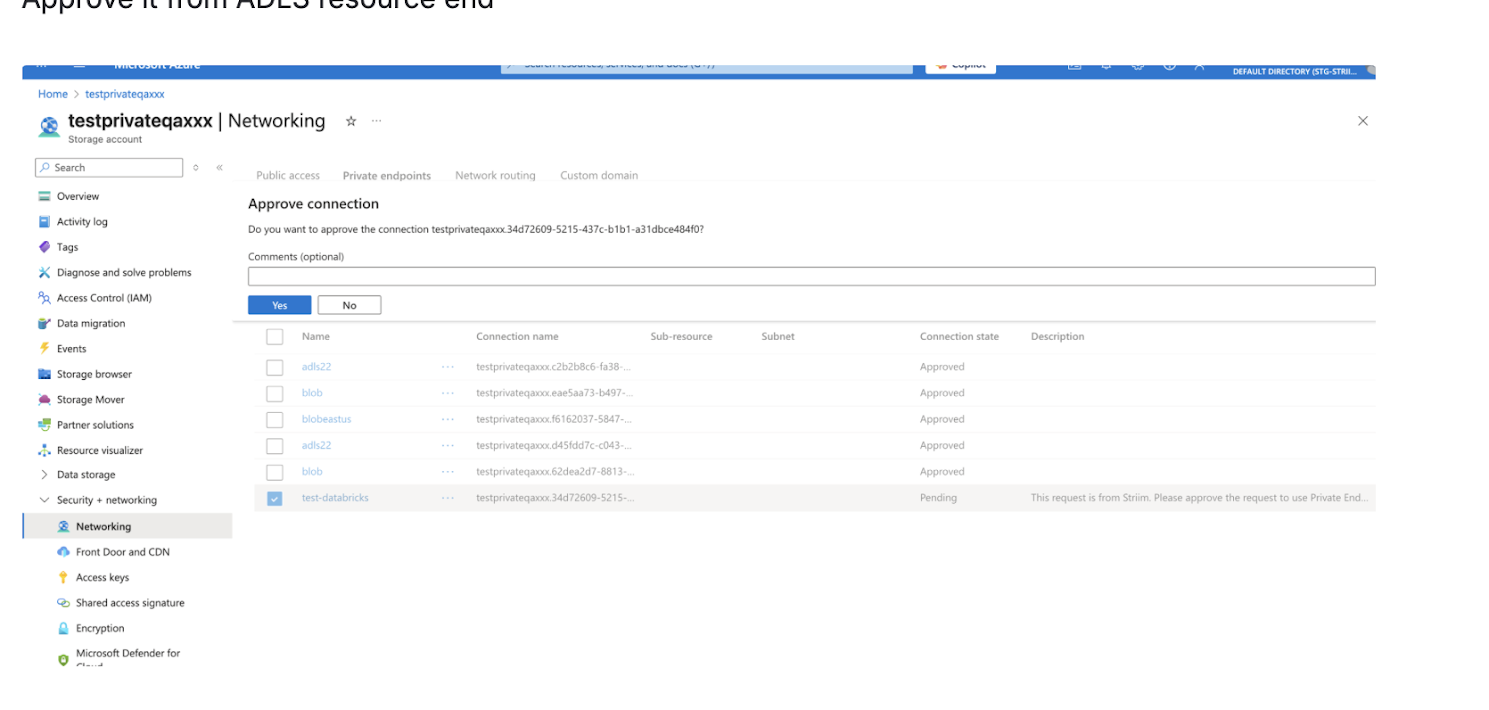
Approve the request to establish the private endpoint connection.
After approval, the private endpoint connection is established between Striim Cloud and Azure Storage.
Configure Fabric Data Warehouse Writer
Configure Fabric Data Warehouse Writer to use trusted workspace access.
Create a connection profile for the Fabric Data Warehouse endpoint.
Create a connection profile for the ADLS Gen2 endpoint.
In the Fabric Data Warehouse Writer configuration, enable the Trusted Workspace Access toggle.
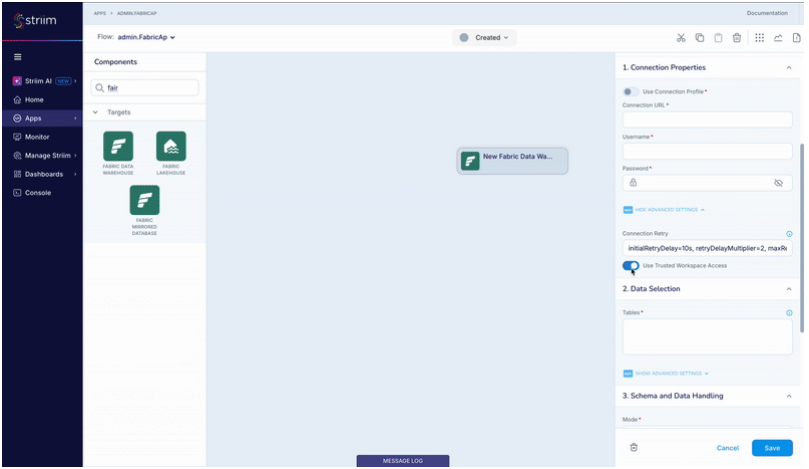
Save the configuration.
Troubleshooting
Issue | Possible cause | Resolution |
|---|---|---|
Access denied to storage. | Missing role assignment. | Verify the Storage Blob Data Contributor role is assigned to the workspace identity. |
An application has been configured to use workspace identity, but no workspace identity is attached to a workspace. | Workspace identity not enabled. | Enable workspace identity in the Fabric workspace settings before deploying the application. |
File cannot be opened because it does not exist or is used by another process. | Application configuration issue. | Undeploy the application to edit it. After fixing all errors, resume the application. |
Fabric Data Warehouse Writer data type support and correspondence
TQL type | Fabric type |
|---|---|
Binary | varbinary |
Boolean | bit |
Byte | smallint |
Date | date |
DateTime | datetime2 |
Decimal | decimal |
Double | float |
Float | float |
Integer | int |
Long | bigint |
Short | smallint |
String | char, varchar |
Time | time |